

Alignment Between Business and Information Security Improves with Maturity: What’s the Impact and Which “Side” Needs to “Mature?” (Part 2)
Blog Post
Alignment Between Business and Information Security Improves with Maturity: What’s the Impact and Which “Side” Needs to “Mature?” (Part 2)
Demetrios Lazarikos (Laz)
March 18, 2022
A Recap
In our first installment of this series, we acknowledged that a successful CISO is often required to align their needs with business leaders who might carry different points of view. We questioned if those differing points of view would ever align. Blue Lava compiled data gathered through research and reviewed a fairly extensive list of research reports and frameworks (including Blue Lava’s own CISO program framework) to draw some insights to address two key questions:
What expectations do those on the business side of an organization have of their CISOs?
What are the CISO priorities as they think about managing their own teams and programs?
First, How We Got Here: The Methodology
Before we get into the findings this week, we want to refresh you on how we collected the data.
We initially gathered frameworks and articles from a total of 10 reputable research and analyst firms. Additionally, we added our own community-driven data to support the study. *see cited sources below
We took the data and categorized it into two dimensions and aligned those categories to see where there were citations of either business expectations or CISO priorities in the arranged categories. We were able to identify a total of 88 citations across 14 Infosec categories and 15 business community categories.
The data brought forward two viewpoints – what the business community is expecting and, in comparison, what the infosecurity community is focused on. To create the graph below (Figure 1), we simply organized and analyzed the number of citations per category. It emphasizes possible correspondences and discrepancies between expectations and priorities on both sides.
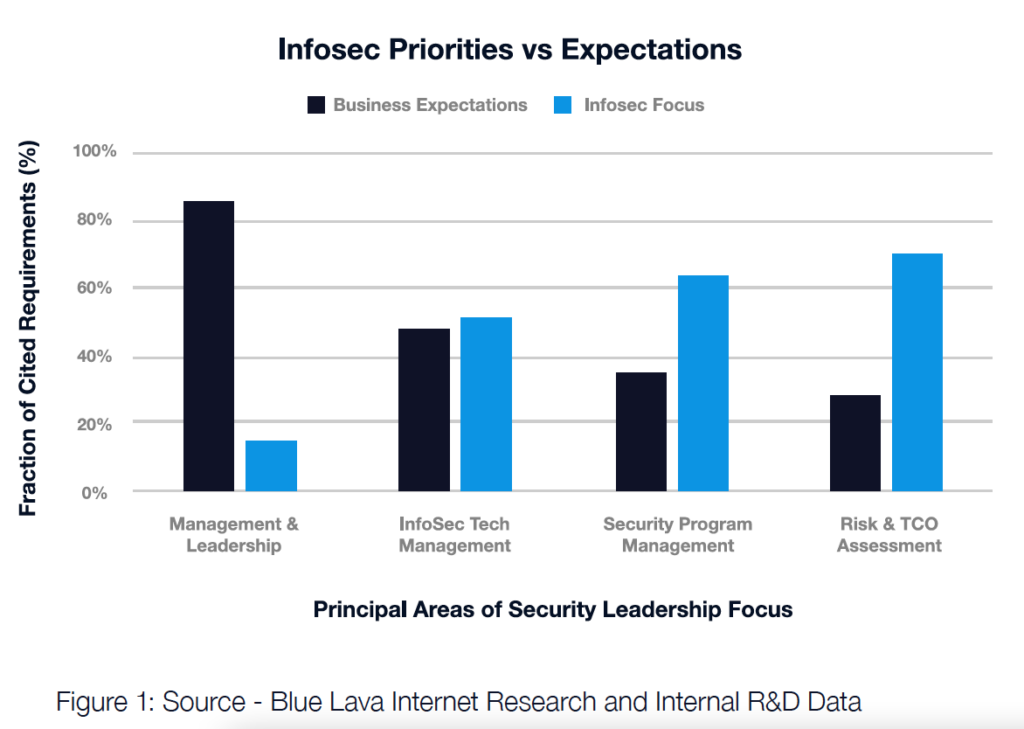

Our comparison suggests a few things. First, there are apparent gaps in conversions held between CISOs and business leadership teams. Expectations on deliverables on either end are not being met. Second, our findings showed that CISOs actions and investments don’t directly align to business goals. This could possibly put future investments and budgeting in jeopardy. Finally, while we admit this is a rather impressionistic study, it suggests that a key to mending these issues between the two groups could be as simple as them taking the time to learn each other’s tactics, vernacular, and strategic concepts.
Overall, we believe these hypotheses indicate this is merely a matter of the languages each group speaks. While likely confident in their individual business strategies and actions, neither side is getting through to each other. But, could it be that simple? We hope the content will answer that very question.
The Breakdown
In this series, we will discuss the results by breaking the chart and data down into three primary sections:
On the left: General Management and Leadership
In the middle: Information Security, Technology, and Program Management
On the right: Risk and Total Cost of Ownership
Last week we started in the middle category, Information Security, Technology, and Program Management, where we identified an apparent alignment in vocabulary and taxonomy. This alignment suggests that the business community and InfoSec leadership have a fairly common implied concern, and therefore a similar set of priorities, when it comes to managing the technology and security programs in support of the business.
This week we take a look at the right side of the results – Risk and Total Cost of Ownership.
Analyzing the Right: The Risk Appetite is Unclear
Continue to move to the right to the Risk and TCO section, and we can begin to see some bigger disconnects in both perspectives and expectations when it comes to how each group views and discusses risk and return. This is where things start to diverge a bit.
From the InfoSec leadership perspective, there’s a clear focus on vulnerabilities, attacks, incidents, and threat intelligence. From the business community perspective, there’s an expectation generally being met, operationally, in these same areas.
Worth noting in this section are two areas of notable divergence: the definition of risk appetite from the business perspective (lacking in the InfoSec leadership language) and the value of fraud prevention from the InfoSec perspective (lacking in expectations from the business community).
As a CISO, the results here may present themselves in how you communicate your program to the business versus how it is received by your business community audience. Chances are that the effort you put into managing an information security program is probably significantly under-appreciated—the majority of the risks you worry about don’t seem to resonate with the business leadership team. What is the company’s risk appetite, and is the InfoSec leadership team managing to that? And with that, the budgets, metrics, and outcomes you focus on and report out against could fall flat from their perspective.
Naturally, this makes sense as the InfoSec teams are often technically driven with a deep focus on the threats to the technology stack and the operational risks that this brings to bear. However, the lack of terminology and vocabulary to convert that technical risk to business risk could be doing a disservice to the security leadership team.
In the upcoming third and final part of this series, we will examine the findings in the left category – General Management and Leadership and summarize our overall findings. Be sure to follow us on LinkedIn to be notified of new content we publish.
Cited Sources:
- “ESG Presentation – “Cyber in the C-suite and Boardroom””
- Blue Lava framework categories
- “Predicts 2021: Cybersecurity Program Management and IT Risk Management” – Gartner
- “Are CISOs Meeting Market Demand? A Benchmarking Report on What Organizations Look for in a CISO and How Candidates Compare” – Gartner
- “CISO Effectiveness: A Report on the Behaviors and Mindsets That Impact CISO Effectiveness” – Gartner
- “Principles for Board Governance of Cyber Risk” – INSIGHT REPORT, MARCH 2021
- “Boards and cybersecurity” – McKinsey & Company
- “Cybersecurity: Emerging challenges and solutions for the boards of financial-services companies” – McKinsey & Company
- “COVID-19 crisis shifts cybersecurity priorities and budgets” – McKinsey & Company
- Rethink your cyber budget to get more out of it – PWC




